May 29, 2023
Doctor Web has detected a spyware-capable Android software module. This module gathers data on files present in the devices and can send them to malicious individuals. Additionally, it has the ability to replace and upload clipboard contents to a remote server. Named Android.Spy.SpinOk as per Dr.Web’s classification, this module is circulated as a marketing SDK. Developers have the option to integrate it into various apps and games, including those accessible on Google Play.
The SpinOk module presents itself as an enticing feature aimed at engaging users through mini-games, task systems, and the promise of rewards and prizes. However, beneath its appealing facade, this trojan SDK carries out a malicious agenda. Upon activation, it establishes a connection with a C&C server, transmitting a substantial amount of technical data about the infected device. This information includes readings from various sensors like the gyroscope and magnetometer, enabling it to detect emulator environments and dynamically adjust its operations to evade detection by security experts. To further conceal its actions, the module disregards device proxy settings, ensuring that network connections remain hidden during analysis. As a result of this exchange, the module receives a list of URLs from the server, which it proceeds to open in WebView to display advertising banners, promoting the execution of its deceptive schemes.
Some examples of ads Android.Spy.SpinOk displays:

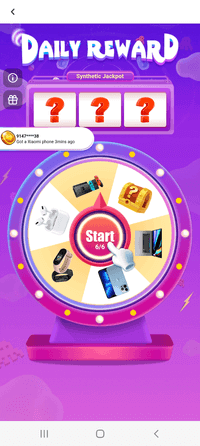
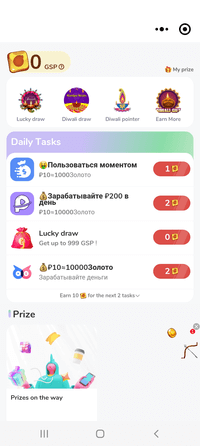
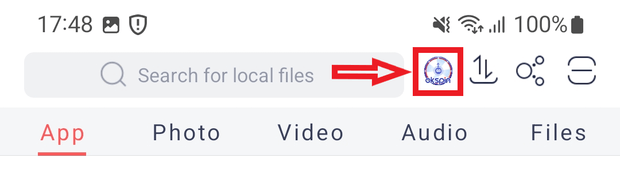
At the same time, this trojan SDK expands the capabilities of JavaScript code executed on loaded webpages containing ads. It adds many features to such code, including the ability to:
- obtain the list of files in specified directories,
- verify the presence of a specified file or a directory on the device,
- obtain a file from the device, and
- copy or substitute the clipboard contents.
This allows the trojan module’s operators to obtain confidential information and files from a user’s device—for example, files that can be accessed by apps with Android.Spy.SpinOk built into them. For this, the attackers would need to add the corresponding code into the HTML page of the advertisement banner.
Doctor Web specialists found this trojan module and several modifications of it in a number of apps distributed via Google Play. Some of them contain malicious SDK to this date; others had it only in particular versions or were removed from the catalog entirely. Our malware analysts discovered it in 101 apps with at least 421,290,300 cumulative downloads. Thus, hundreds of millions of Android device owners are at risk of becoming victims of cyber espionage. Doctor Web notified Google about the uncovered threat.




Below are the names of the 10 most popular programs found to carry the Android.Spy.SpinOk trojan SDK:
- Noizz: video editor with music (at least 100,000,000 installations),
- Zapya – File Transfer, Share (at least 100,000,000 installations; the trojan module was present in version 6.3.3 to version 6.4 and is no longer present in current version 6.4.1),
- VFly: video editor&video maker (at least 50,000,000 installations),
- MVBit – MV video status maker (at least 50,000,000 installations),
- Biugo – video maker&video editor (at least 50,000,000 installations),
- Crazy Drop (at least 10,000,000 installations),
- Cashzine – Earn money reward (at least 10,000,000 installations),
- Fizzo Novel – Reading Offline (at least 10,000,000 installations),
- CashEM: Get Rewards (at least 5,000,000 installations),
- Tick: watch to earn (at least 5,000,000 installations).
The full list of apps is available via this link.
Dr.Web anti-virus for Android successfully detects and neutralizes all known versions of the Android.Spy.SpinOk trojan module and programs that contain it, so this malicious app poses no threat to our users.
More details on Android.Spy.SpinOk

