netdummyadmin
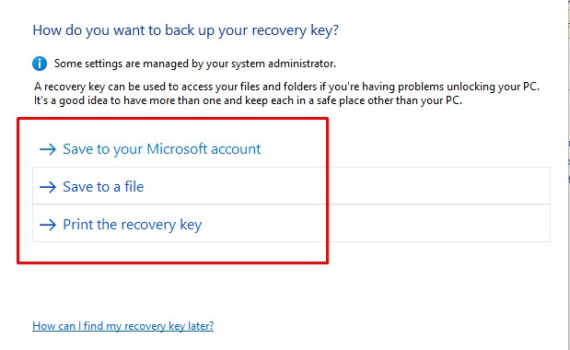
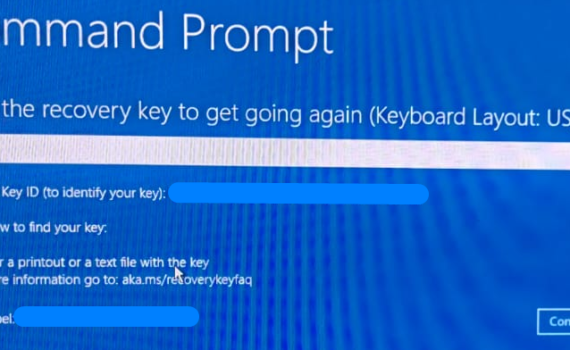
Having bitlocker encryption enabled on your portable device adds a layer of security against snooping in situation when you lose or misplace it. Without password, the drive is encrypted and inaccessible even if it is booted using an alternative bootable media. Active Directory or Azure AD joined devices will have […]
Azure AD Join in Microsoft Azure Active Directory that allows organizations to extend their traditional on-premises Active Directory to the cloud. Bitlocker encryption is enabled by default and keys are backed up to Azure AD. Changes to UEFI settings, changes in hardware, attempts to bypass boot process via changing the […]
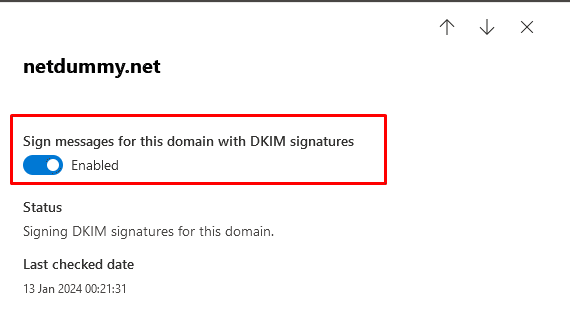
Anti-SPAM implementation covers filtering and blocking incoming spam on receiving and verifying the sender’s allowed hosts thus preventing the likelihood of your users becoming the target of a Joe job that will flood their inboxes with bounced mails when their email addresses are spoofed as the sender. Combination of SPF, […]
Simultaneous Authentication of Equals (SAE) is a secure key exchange protocol that’s used in Wi-Fi networks, particularly in WPA3 (Wi-Fi Protected Access 3). It’s designed to improve the security of the initial authentication process when a device connects to a Wi-Fi network, replacing the pre-shared key (PSK) method used in […]
WPA3 (Wi-Fi Protected Access 3) is the latest security protocol for Wi-Fi networks, succeeding WPA2. It was introduced to address vulnerabilities and enhance security features over its predecessor. Here are some key features of WPA3: WPA3 is designed to improve the security of Wi-Fi networks and address some of the […]
In today’s tech-driven world, mobile devices such as smartphones and tablets play an integral role in our personal and professional lives. To make the most of these portable powerhouses, users rely on a wide range of tools and apps that enhance productivity, security, and overall user experience. In this article, […]
Dutch cybersecurity consultancy, Midnight Blue, revealed their research findings called “TETRA:BURST,” which involves a cryptographic bug in the TETRA (Terrestrial Trunked Radio) system, commonly used by law enforcement and emergency services. Unlike modern encryption algorithms, TETRA’s 1995-era encryption remains in use, largely because it is proprietary and guarded under non-disclosure […]