How to get all your corporate “Ops” teams working together, with cybersecurity correctness as a guiding light.
You may also like
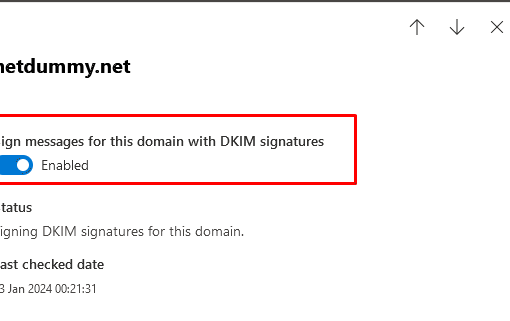
Anti-SPAM implementation covers filtering and blocking incoming spam on receiving and verifying the sender’s allowed hosts thus preventing the likelihood of your […]
Here’s a brief reminder to do two things. The first is to patch. The second is to read up why it’s a […]
WPA3 (Wi-Fi Protected Access 3) is the latest security protocol for Wi-Fi networks, succeeding WPA2. It was introduced to address vulnerabilities and […]
Latest episode – check it out now!